Approach to achieve Cyber Resilience

Governance
All organizations must adapt a governance framework which is primarily focused on how the information security activities of the organization are directed and controlled in terms of tools, personnel and business processes to ensure that information security is adequately managed and applied to the information assets in order to meet the organizational objectives.
Governance can be exercised in the way of establishing an information security organizational structure and steering committees, developing Information Security Action Plans and allotting the necessary funding for Information Security activities, defining roles and responsibilities of the IT Security team alongside the reporting lines, setting performance measurement indicators and establishing a diversity of IT/business committees.
Guidelines for Implementing the Governance Framework
Achieving better governance starts with the business, and more specifically with understanding its strategy and goals. IT Security should be involved early in the business strategy definition process. The IT Security goals set out in the IT strategy plan should clearly support the achievement of one or more business goals. It is the responsibility of the Information Security Committee (ISC) in collaboration with the Functional Heads to ensure that the IT security strategy is aligned with the business strategy. This could be achieved through:
- Clear business goals, communicated to the entire organization
- Early involvement of IT security in business strategy process
- Align IT security goals to business goals
- Derive IT security strategy from business strategy
After aligning the IT security goals with the business goals, it is important to implement required set of efficient and effective IT governance and management processes through selecting the most critical process based on business priorities, assign process owners, develop metrics and monitor the achievement of process as per set objectives.
Effective Governance is determined by the way the IT Security team is organized and where the IT security decision-making authority is located within the organization. It is crucial to establish the right management structure to ensure there is proper collaboration between business and IT security department.
This could be achieved through:
- Head of the organization [HOO] providing leadership and spearhead initiatives to create and maintain an Information Security Culture within the organization. The responsibility for governance rests with the Head of the organization as he/she is responsible for evaluating, directing and monitoring the governance processes as per stakeholder requirements.
- Appointment of an Information Security Officer (ISO) for the organization who will serve as the principal advisor on matters relating to information security and shall develop the Information Security Objectives, Information Security Programs and action plans whilst ensuring operations comply with the statuary regulations.
- Ensuring the Chief Innovation Officer (CIO) is empowered with Information Security. If the organization does not have a capable candidate to handle the ISO function the CIO can be assigned the role of the ISO through providing adequate training in order to ensure that he/she is able to protect the organization’s information assets.
- Chief Internal Auditor (CIA) is empowered to Lead and Report on Information Security Audit Activities to auditing the implementation of information security initiatives, assessing the organization’s compliance with Baseline Security Standard (BSS), and reporting information security related findings to the Audit and Management Committee (AMC) for further remediation if any.
- Establishment of an Information Security Committee (ISC) to Oversee and Lead Information Security Activities. The ISC responsible for reviewing and approving all Information Security controls and action plans, assets classification schemes, security policies, incident response plans and disaster recovery plans developed by the ISO and shall monitor the implementation of such plans. The Committee should consist of the HOO, ISO, CIO, CIA, and key information and IT asset owners. HOO should chair the Committee.
- Establishment of a Risk Management Committee (RMC), directly reporting to the HOO which has the responsibility of overseeing the risk management of the organization with respect information and IT assets. RMC should identify and evaluate risks in relation to assets and should propose appropriate controls to ISC to take necessary actions to mitigate the risks. RMC shall include Process Owners (sectional heads), Asset Owners, and the ISO. Deputy Head of the organization shall be the chairperson of the RMC.
Successful implementation of governance in organizations requires the effective usage of their IT enabled investments throughout the economic life cycle of the projects based on the Action Plan using best practices of project management as required through;
- Organizational objectives should be analyzed to identify dependencies on information security, and then link information security objectives to overall organizational activities.
- The IT security strategy should be an IT blueprint of the business strategy plan. The IT Security goals set out in the IT strategy plan should clearly support the achievement of one or more business goals.
- Information security strategies or action plans, programs, projects and activities should be designed in a such a way that those initiatives intrinsically linked with organizations objectives and governing principles and approved by the Head of Organization.
- Budgets are to be allotted for information security activities embedded in the action plans.
Whilst the CIA conducts assessments and reviews to ensure that the organization conforms with the Baseline Security Standard and other statuary regulations. The HOO is ultimately responsible for managing and governing information security activities in their respective organizations. However, designated representatives including Information Security Officers, Chief Innovative Officers, and all other staff have distinct roles to play as specified in the Information Security Handbook. To conform to same, it is essential that,
- Metrics shall be set and monitored to ensure successful implementation of the Baseline Security Standard considering the organization’s level of maturity thereby identifying gaps and ensuring corrective action is to be taken as required.
- To ensure that individuals adopt and execute upon their roles and responsibilities, a process of formal evaluation and regular process of review is to be implemented as part of performance management.
Identification
In terms of the Identify function, its primary objective is to assist organizations to understand their ICT resources that include systems, people, assets, data, and capabilities and the risks associated with resources in order to manage cybersecurity risk.
An Information Asset is any information that has a value to the organization to perform its organizational functions. The organization must identify all assets and provide adequate protection to the said assets. Identification of information assets must be done with an intention of protecting assets from unauthorized access, use, disclosure, disruption, modification, or destruction in order to ensure integrity, confidentiality, and availability of assets.
Organizations should establish, record and maintain an Information Asset Register (IAR) which is a formal catalogue (inventory) of all security classified information assets an organization holds and processes that is to be maintained at a central location. The Information Asset Registry should be accurate, up to date, consistent and aligned with other inventories. It is the responsibility of the Deputy HOO to ensure that the IAR is formulated and maintained. The RMC, in concurrence with the IAO shall develop the IAR.
and other users.
The IAR should include the following:
- Name or unique identifier of asset or group of assets;
- Description of information asset;
- Location of information asset, including the device on which it is stored;
- Information owner and information custodian;
- Classification of the information asset;
- Date of classification with details of the authority of the classifier; and
- Reason for the classification of the information asset
- Date to review classification (if known)
- Users and usage of the information
- Number of copies in circulation and their location
- Disposal details where information has been disposed of (if applicable)
The IAR should have a default classification of CONFIDENTIAL because of the detail it provides on other security classified information. It is to be reviewed and maintained at least annually to ensure it meets the requirements of the Sri Lanka Government Information Classification Framework and organizational needs.
IT Assets are servers, computers, storage devices, networks and networking devices, software or any other digital infrastructure which has a value to the organization. It is the responsibility of the Deputy HOO to ensure that the AR is formulated and maintained. The RMC, in concurrence with the IAO shall develop the AR.
The IT Hardware Asset registry shall contain at a minimum,
- Device Name
- Serial Number
- Machine reference / Label if any
- Type of Asset
- User
- Location
- Risk Exposure
- Classification
- Purchase date
- Warranty period
- Warranty expiration
- Vendor supplier detail
- Printer/Scanner
- HDD / RAM if applicable
- License Details
- Operating System
The IT Software Assets registry shall contain at a minimum,
- Software Description
- Application Identification Number
- Application Name
- Description
- Version
- License Information
- License Type
- Expiry/Renewal Date
- Serial Number
- Qty Purchased
- Purchase Information
- Purchase Date
- Purchase Order / Payment Voucher No.
- Purchase Cost
- Vendor Name
- Contact Person
- Contact No.
The IT Asset Registries should be accurate, up to date, consistent and aligned with other inventories.
An Asset Owner and Custodian should be identified for each Asset. An Information Asset Owner is an individual who has the responsibility for controlling the whole lifecycle of an asset. The Custodian of the information asset will be responsible for the protection of the asset and for implementing the controls (as identified and approved by the owner of the information asset) related to the protection of the asset. Owner and Custodian is responsible for managing the entire lifecycle of the asset – from creation, modification to destruction. HOO, in concurrence of the Functional Heads shall nominate an IOA/CA.
Organization should identify the users who should have access to Information Assets and IT Assets. User should be identified based on the on the Need-to-Know and Need-to-Use principles.
In the Need-to-know principle, users are only granted access to the information they need to perform their tasks In Need-to-use principle, users are only granted minimum privilege access to IT Assets that needed to perform their task or job.
RMC in collaboration with IAOs, should conduct a comprehensive risk assessment to determine the threats to and vulnerabilities of the organization’s assets, and their impact on Assets. Objective of the risk management is to
- Asset Identification, in which the RMC shall identify all information assets and collect relevant data to identify IT related risks associated with assets.
- Evaluate threats and vulnerabilities, associated with the information assets and the likelihood of their occurrence.
- Evaluation of Impact, The outcome of a threat exploiting a vulnerability is the Impact. The Impact can vary in magnitude and will be attributable to the severity of the breach and the time. The RMC should identify all potential impacts of the threats.
- Calculation of Risk, The RMC should implement a risk calculation process to estimate risk exposure to assets by taking into consideration the probability of occurrence and magnitude of the impact. Thereby, a risk level matrix is to be defined to calculate the risk exposure
- Evaluation of and Response to Risk Exposure – The RMC is to develop a Risk response plan/strategy in terms of Risk mitigation, acceptance, avoidance and Transfer. The countermeasures should be identified in terms of preventive, detective and corrective controls. Furthermore, Periodic reviews should be conducted to review the risks identified and its outcomes.
RMC should classify Assets (Information Assets and IT Assets) to ensure that assets receive an appropriate level of protection in accordance with legal & operational requirements, value, criticality and sensitivity to unauthorized disclosure or modification whilst taking into consideration the level of impact to the organization if confidentiality, integrity or availability of the particular organization is compromised.
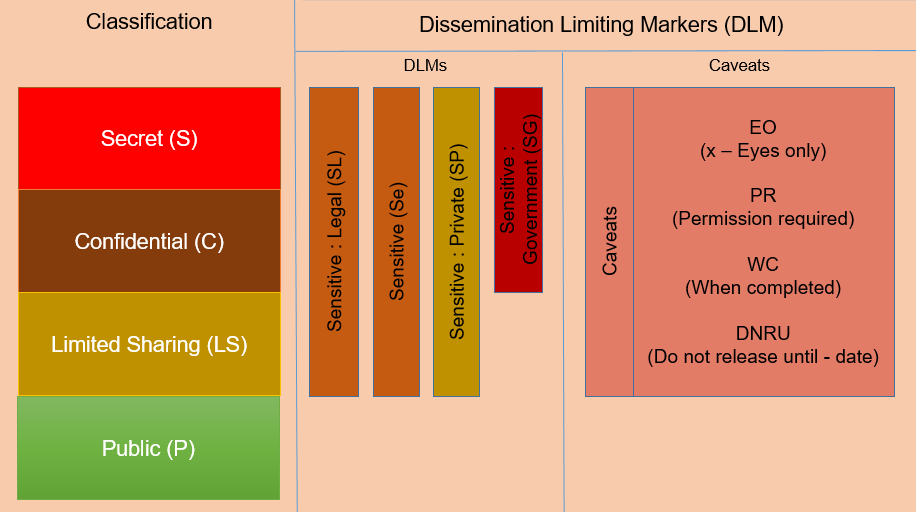
Levels of Security Classification
Broadly, five levels (four classification levels plus - Unclassified) of security classification have been defined as part of the Information Classification Framework including Unclassified, Pubic, Limited sharing, Confidential and Secret.
All Government information, until such time they are evaluated and classified, must be allocated the interim classification status “Unclassified”. Any unclassified information should be treated similar or higher to information classified as Limited sharing.
Prior authorization must be obtained from the information owner to release unclassified material to the public (which is in effect changing the classification of the information).
Any information which is easily available to the public, Government employees, organizations, regulators, project managers, support staff and contractors including information deemed public by legislation or through a policy of routine disclosure can be classified as “Public”. This type of information requires minimal or no protection from disclosure. Examples of public information include:
- Government acts and policies;
- Organization contact persons;
- Information on public services provided to citizens by Government;
- Weather Information; and
- Advertisement for job postings.
Information is security classified as “Limited Sharing” when compromise of information may lead to minor probability of causing limited damage to Sri Lankan Government, commercial entities or members of the public. Unauthorized disclosure of this information will cause negligible or no damage to internal security, Sri Lankan forces or Sri Lanka ‘s foreign relations. Examples of Limited sharing information are:
- Organization processes and information
- Personal information of citizens
- Minutes of meetings and file notes of Organizations
- Government evaluation on a company’s products
- Inventory data
Information is classified as “Confidential” when compromise of information may lead to a high probability of causing damage to national security, internal stability, national infrastructure, forces, commercial entities or members of the public.
In the case of material marked ‘CONFIDENTIAL’ the information asset is subject to the disclosure of which may be limited or prohibited. Examples of Confidential information are:
- Personal case files such as benefits, program files or personnel files
- Tax returns or financial health of organization
- Sharing of personal health information of individual
- Trade secrets
- Salary information
Information is classified as “Secret” when compromised could cause serious damage to national security, Government, nationally important economic and commercial interests or threaten life. It could also raise international tension and seriously damage relations with other governments, shut down or substantially disrupt significant national infrastructure and seriously damage the internal stability of Sri Lanka or other countries. Examples of Secret information are:
- Details of sex offenders and victims;
- Criminal investigations for major crime;
- Data related to foreign affairs;
- Cabinet documents; and
- Provincial Budget prior to public release.
The diagram below represents Sri Lanka Government Information Classification model details of each of elements are described in sections below:
Protection
The Protect Function facilitates all organizations to take appropriate measures in terms of developing and deploying appropriate defenses to ensure delivery of IT services in order to limit or contain the impact of a potential information security event.
Information Security awareness and training are critical components of the information security strategy of a organization as they are means of disseminating required instructions to employees that they need to ensure information security in the process of performing their duties.
It is a global phenomenon that 95% of cyberattacks and information security breaches are due to human error. Therefore, it is crucial that organizations should;
1.1 Develop the information security capacity of staff at different levels across the organization through conducting awareness and trainings.
1.2 Awareness trainings and workshops should be carried out on an ongoing basis which should be incorporated as a vital component in the annual training plan of the organization.
It is vital that appropriate measures to protect assets in terms of ensuring confidentiality, integrity, and availability of information. Following measures should be taken to protect assets.
2.1 Organizations must protect assets based on classification
The organization shall ensure that the classified assets are protected in terms of maintaining confidentiality, integrity, and availability of information according but not limited to the controls listed below that has been endorsed to protect the information asset.
2.1.1 Protecting Data-at-Rest
Data at rest is data that is not actively moving from device to device or network to network (e.g. data stored on a server, cloud, hard drive, laptop, flash drive, or archived/stored). It is essential to encrypt any data classified as Secret or Confidential (information assets) prior to storing. Organization must control access to data at rest by implementing access controls as specified in the latest version of the Information Security Implementation Guide.
2.1.2 Encrypting Data-in-Transit
Data in transit is the data that is actively moving from one location to another such as across the Internet or through a private network (e.g. data being transferred from site A to B through a public network). In order to protect data in transit, organizations should encrypt sensitive data prior to moving and/or use encrypted connections (HTTPS, and latest versions of SSL, TLS, FTPS, etc.) as prescribed in the latest version of Information Security Implementation Guidelines.
2.1.3 Physical Protection of Assets
Based on the classification of assets, organizations are to setup a physically secure environment to store and/or process classified assets. Demarcated areas are to be used to securely store or process critical assets. Secure which should include but is not limited to controls such as
- Physical perimeters demarcated as secure rooms with physical walls and lockable doors, Lockable and Fireproof Safes
- Multi-factor entry systems
- Continuous CCTV Monitoring
- Fire suppression systems in place
- Water detectors and Temperature sensors installed
- Surge protectors and UPSs
- Raised floors
Logical Access to the computers, systems or any devices should be regulated and closely monitored.
Information assets classified as SECRET, CONFIDENTIAL, and LIMITED SHARING must be stored and processed in Secure Areas.
External photographic or video equipment should not be allowed within secure areas and only authorized staff shall be allowed to work within the secure areas. Organizations must not permit staff to bring non organization owned devices to highly secure areas.
2.1.4 User Access Management
Logical access controls are the features of IT system (or equipment) that enable authorized personnel access to resources. It controls an individual’s ability to access computers, systems, databases or digital infrastructure through the implementation of user ID and passwords, access cards, biometrics, tokens or other mechanisms.
To control access, each organization should develop and implement an Access Control Policy, which is built on the “need-to-know” and “need-to-use”/ “minimum privilege” principles. Users are only granted minimum access to Information Assets to which they need access in order to perform their task (“need-to-know”), and users are only granted minimum access to IT Assets (equipment) that those users need to perform their tasks (“need-to-use”). User Registration and Assigning User IDs, Privilege Accounts Management, Shared User Account Management, User Password Management, User Transfers and Terminations, Validation of User Accounts, Application Access Control, Operating System Access Control and Access to Networks and Network Services are covered under the Access Control Policy. All government employees including third party contractors should adhere to the Access Control Policy of the organization. Matters related to access controls should be handled by the ISO.
2.1.5 User Access Management
All organizations should implement strong passwords for all user accounts which are used to access information systems of the organization. Password must be at least 8 characters long and it must consist of both upper and lower case characters (e.g. a-Y), and digits (1,9), and special characters (!@$+/). In a situation where the multifactor authentication cannot be implement, organization should set a password expiry. All passwords must be changed after predetermined intervals which is 30 days for privileged access IDs and 90 days for regular access.
| Password Configuration Settings | |
|---|---|
| Minimum Password Length | 08 Characters |
| Maximum Password Age [ End User ] | 90 Days / MFA |
| Maximum Password Age [ Privileged User ] | 30 Days / MFA |
| Minimum Password Age | 01 Day |
| Password History | 13 passwords remembered |
| 1st Login Change | Enabled |
| Password complexity | Enabled |
| Account Lockout Configurations | |
| Account Lockout threshold | 5 invalid login attempts |
| Account Lockout Duration | Lock the user indefinitely until Administrator unlocks |
| Reset Account Lockout reset Counter | 1440 minutes |
2.2 Organizations Should Segregate Duties
Segregation of duties is to be performed to avoid collusion, thus assures that no single employee can access, modify or use critical information (IT assets that use critical information) without authorization or detection. It will thereby reduce opportunities for unauthorized or unintentional modification or misuse of the organization’s information assets.
At the discretion of the HOO, Information Assets are to be segregated among authorized personnel to ensure information security.
Each organization should avoid conflicting duties and areas of responsibility shall be segregated to reduce opportunities for unauthorized or unintentional modification or misuse of the organization’s critical information assets. Any activity done by a both end users as well as privileged users should be traceable and logged.
2.3 Organizations Should Ensure Email Security
Email security involves adoption of different procedures and techniques for protecting email accounts, content, and communication against unauthorized access, loss or compromise. Following measures should be taken in order to ensure email security.
2.3.1 Official Emails for Official Communications
Each employee should use their official email addresses with the domain “.gov.lk” provided by the organization for official communication.
Users must not use personal email accounts for official communications and their official email for personal correspondence. All email attachments, regardless of the source or content, must be scanned for viruses and other destructive programs before being opened or stored on any organization’s computer system.
All employees must adhere to Safe and Appropriate Use of e-Mail Guidelines as prescribed in the Information Security Implementation Guide.
2.3.2 Secure Configuration of Email Accounts
In the instance that the organization operates its own mail server, the hosting site should be located within the Jurisdiction of Sri Lanka. Organization shall set up email filters to remove emails known to have malware attached and prevent inbox from being cluttered by unsolicited and undesired (i.e. “spam”) email. Organization should also ensure Domain-based Message Authentication Reporting and Conformance (DMARC), Domain Keys Identified Mail (DKIM) and Sender Policy Framework (SPF) are records are in place for their domains to make email spoofing difficult. Such organizations should also adhere to the email security technical guidelines as prescribed in the Information Security Implementation Guide.
If the email accounts supplied by the Lanka Government Network (LGN), Information and Communication Technology Agency (ICTA) should ensure that the email service is securely configured (E.g. Enabling of Spam protection and Phishing) and security audit reports should be supplied to Sri Lanka CERT on periodic basis.
2.4 Usage of Digital Signatures and Encryption
It is advisable that Organizations should use digital signatures to digitally sign the emails, messages and other documents. Furthermore, when sending confidential information via emails, it must be encrypted.
2.5 Data Sovereignty
Organization should not store, process data, or host software applications (including web applications) in other jurisdictions. It is vital that’s the Organization should comply the legal requirements of the forthcoming Data Protection Law and Cyber Security Law of Sri Lanka.
2.6 Following Security-by-Design Approach in Software Development
In software development, it is essential that the concept of security is incorporated into the design of the software from inception. Security-by-Design extends to integrating security consideration to each stage of the software development lifecycle.
In developing software, the organization must consider security planning and risk assessment at the initiation stage, defining security requirements in the vendor selection stage, reviewing security architecture in the design and development stage, reviewing the code for vulnerabilities at the coding stage, vulnerability assessment in the implementation stage, and secure disposal at the system decommissioning stage approach.
2.7 Conducting Periodic Information Security Audits
The organization should have a formal Internal Audit program in place, to conduct routine audits that includes but is not limited to IT control audits, Application control reviews, Network architecture reviews, IT process audits, compliance reviews, internal and external vulnerability assessments, penetration testing, web application penetration testing which should be performed periodically.
Furthermore, a formal process to oversee the implementation of recommendations raised in previous IT Audit reports is to be established. Chief Internal Auditor of each Ministry should coordinate audits of the organizations under its purview.
2.8 Perform periodic Vulnerability Assessments and Penetration Tests
Prior to the deployment of any website, web application or system on the live environment, the organization must obtain the services of Sri Lanka CERT to conduct Vulnerability Assessments and Penetration tests (VAPT) as and when required.
The organizations must perform VAPTs for their applications, at least annually and, it is a must to conduct VAPT before a system/device is first deployed, after an incident, after a change is made to the application, after changes to the platform or hosting environment, after changes to standards, policies and guidelines, after spread of virus/malware, and as determined by the RMC/ISC.
2.9 Using Licensed and Up-to-date Software
Organization should use operating systems and other relevant software with valid License(s). If organizations do not maintain licensed Operating Systems, it could render them vulnerable to risks such as Privacy intrusion and loss of sensitive data, Legal Prosecution, Limited or no support from vender, Compromised system security and stability due to modifications, Spyware and rootkits and productive time consumed to fix the system problem which impedes day to day operations.
Organizations shall update operating systems and other relevant software with vendor supplied latest patches and fixes. Whenever appropriate, organization should enable automatic updates.
2.10 Installation of Anti Malware Software
The CIO of the organization shall ensure that a malware protection solution with a valid license is installed and running on all servers and workstations whilst ensuring that antimalware tools remain active at any potential entry point.
It is ideal if malware protection on servers is centrally managed. Forced software updates are to be applied to all devices as soon as new releases are available within an acceptable timeframe, but at least on a monthly basis. Malware signature of antimalware software should be up-to-dated and automatic update should be enabled.
Malware detection must be configured for on-access scanning, including downloading or opening of files, folders on removable or remote storage, and web page scanning. Users must be prohibited from changing the configuration of, uninstalling, deactivating or otherwise tampering with any Virus and Malware prevention/detection software that has been installed on systems used by them. Externally uploaded data to the organization's file sharing services is scanned for malware before it is internally distributed.
2.11 Installation of Firewalls
To protect organization’s Assets, organization should install a Firewall and appropriately configure Firewalls to protect their networks. Organization shall regularly update their Firewalls and shall install endpoint antimalware with automatic updates enabled. Default Firewall settings should be updated with appropriate configurations, and default vendor supplied user accounts should also be disabled. Firewalls should be configured in accordance with the Information Security Handbook.
2.12 Securing Remote Access
Remote access brings many information security threats to organizations. To mitigate the risk, organizations should use secure Virtual Private Networks (VPNs), allow only the authorized users to access to systems based on the Access Control Policy of the organization, implement multifactor authentication and enable policies with restricted log on hours.
2.13 Hardening of Systems
The organization must take efforts to harden systems and its corresponding components and infrastructure to reduce their surface of vulnerability by eliminating potential attack vectors and condensing the system's attack surface. Hardening systems shall only be done with the support of experienced and skilled personnel. All servers and workstations shall be configured to prevent the execution of unauthorized software.
2.14 Establishing a Backup Strategy
The organization should backup data, logs, systems, software, configurations details and any other information that are necessary to restore normal operations in an event of a disaster. Without periodic formalized backup procedure established it would be difficult for the entity to face the challenge of recovering from a disaster or even a security incident. The above situations would have serious consequences on the operational continuity of the entity not to mention the loss of reputation.
Data written to backup media should be preserved as per the regulatory requirements of the government. Backups should be stored in offsite secure location which is physically distant from the data processing site. Backups containing information assets labeled as secret and confidential should be stored as per the security requirements specified in the Assets Registry. Without periodic backups the integrity, availability and recoverability of data is at risk. It may lead to lengthy business interruptions depending on the nature of the disaster.
Organization should also define Recovery Time Objective (RTO) and Recovery Point Objective (RPO) to determine the frequency of backups. Organization shall ensure that the Backup procedures are well documented and staff is trained. Organizations must make backups of data, applications, configuration data, logs and other relevant software.
2.15 Maintaining a Disaster Recovery Plan
The organization should implement a formally documented Disaster Recovery Plan which is drill tested for operational efficiency to face any challenge posed by an incident or disaster which affects the entity business continuity.
The Disaster Recovery plan aids reduce the time between a disaster occurring and critical functions of the systems being restored. It should contain activities to be performed to recover from a disaster, and roles and responsibilities of each team member assigned to activate plan.
Disaster recovery plan is designed by conducting a risk assessment and business impact analysis of the critical information assets and IT assets, and the recovery activities should be designed by considering the earliest point in time in which it is acceptable to recover the data (RTO), and earliest point in time at which the organizations operations and systems must be resumed after a disaster (RPO). The disaster recovery plan should be tested and updated on a periodic basis through a drill test for operational efficiency to face any challenge posed by an incident or disaster which affects the entity business continuity.
2.16 Develop an Incident Response Plan
The Incident Response Team of the organization should design and develop an incident response plan to prevent incidents which construe of a set of instructions to detect, respond, and recover from information security incidents.
Incident response plan should contain, at a minimum, incident reporting procedures, strategies for detection, analysis and, containment of incidents (eradication or recovery), allocation of information security responsibilities to designated staff, and procedures related to post-incidents reviews. It is crucial that the plan should be tested and communicated to all staff members of the organization.
2.17 Secure Disposal of Information Assets
Assets should be disposed securely using a formal procedure when no longer required. If systems consist of media containing information assets are no longer required, the information assets should be deleted in an unrecoverable manner to prevent the retrieval of the original information.
Low level sector-based formatting, shredding or punching are possible methods of disposing information assets containing in media.
Detection
The Detect Function when deployed to organizations will enable the proactive development and implementation of suitable activities to ensure the timely identification or the detection of occurrence of information or cyber security incidents. These incidents could cause significant financial losses, data losses, reputational damages and sometimes, can even pose threats to the lives of individuals.
It is essential that organizations must enable logging of activities, and events, maintain and retain logs that include but is not limited to Access Logs, Error logs, Server Logs, Event Logs, Audit Logs, Firewall Logs, Virus guard logs for all changes made and activities carried out shall be produced, securely kept and regularly reviewed. It is the responsibility of the ISO to review the logs periodically. Logs can contain sensitive data and thus appropriate measures should be taken to safeguard the said logs against tampering and unauthorized access.
Organizations should develop their capacity to detect incidents through Log Analysis. Organizations shall analyze logs for malicious activities and detect attacks or anomalous activities. Monitoring the events of networks and systems should be ongoing and organizations should implement IPS/IDS to detect attacks and mitigate them on networks and applications.
Alternatively, organizations shall use Security Information and Event Management (SIEM) for basic security monitoring, advanced threat detection, forensics and incident response, log collection, normalization, notifications and alerts, security incident detection. Implementation of Network and IT Infrastructure Monitoring Systems and configuring automated alerts on system failures.
| Tool | Function |
|---|---|
| Network and host Intrusion Detection Systems (IDSs) | Monitor and analyze network and host activity, usually relying on a list of known attack signatures to recognize/detect malicious activity and potential information security incidents. |
| Intrusion Perversion Systems (IPS) | Monitors a network or systems for malicious activity or policy violations and counter detected attacks or anomalous activity (IDS/IPS). |
| Log Analysis | Involves collecting and analyzing event logs using pattern recognition to detect anomalous activities. |
| White Listing | Lists the authorized activities and applications and permits their usage. |
| Black Listing | Lists the non-authorized activities and applications and prevents their usage. |
| Data Loss Prevention (DLP) | Detects potential data breaches/data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data while in use, in motion, and at rest. |
All users should be strictly instructed to immediately report any evidence or suspicious activity/breach of security to the Incident Response Team (IRT). Breaches could include but is not limited to unauthorized access, theft, viruses, vulnerability of an equipment, unauthorized access, presence of any information resource prohibited by guidelines, tampering with information and violation of guidelines or security policy by another user or contractor.
Adequate awareness and trainings should be given to staff on detecting incidents, reporting information security events detected and preserving evidence.
In addition to the incidents reported by the staff, the organization shall invest in tools to detect such instances and the IRT shall develop an Incident register to log the same.
A record should include but is not restricted to;
- The date and time of Occurrence
- Name and Designation of Employee who reported the incident
- Description of the Incident
- Nature of Impact
- Classification
- Root Cause
- Action taken in Response
- Personnel Handling
- Remedial Measures taken to prevent future incidents
- Status of Incident
The organization should install antimalware software on all existing devices or components that are connected to the organization’s network including servers, workstations and any other components. Virus and Malware detection infrastructure should remain active and updated, and configured for on-access scanning, including downloading or opening of files, folders on removable or remote storage, and web page scanning etc. It is the responsibility of the CIO to ensure that virus and malware detection infrastructure remain active and s not disabled at any potential entry point. The detection infrastructure is to be up to date with the latest product and virus signatures as soon as it is released.
If a device is identified as a threat to the organization’s network due to a malware infection, the CIO reserves the right to disconnect the device from the network and isolate it with immediate effect.
Respond & Recover
The Response and Recover processes are to be in place to ensure the viability of the government organization to contain or reduce the impact of an information security event or breach and to enable the organization to resume normal operations after an incident.
Guidelines On Responding To Incidents And Implement Recovery Strategy
In the event of a disaster or a qualifying incident, the Disaster Recovery Plan (DRP) or Incident Response Plan respectively, is to be initiated by the designated authorized personnel through following the course of preplanned actions contained in the formally documented and approved DRP/IRP to minimize the impact on the government organizations’ operations, and to resume normal operations after an disaster/event.
In an event of information security incidents, the organization must apply the relevant incident handling procedures for the containment, eradication and recovery.
Containment - It is crucial that an incident is to be contained before it spreads to avoid overwhelming of resources and increase in damage caused by the incident. The containment strategy shall depend on the nature and impact of the event. Possible courses of action could include disconnecting affected devices from the network, shutting down the affected system, disabling certain system functionality.
Eradication – Find and Eliminate components of the incident that could possibly be the root cause of the breach. This includes but is not limitedto;
- Malware being securely removed
- Systems being hardened and patched, and updates to be applied
- Reviewing remote access protocols and mandating multi-factor authentication
- Change and Harden Access Credentials of End Users and Administrators
Recovery – Restore and Recover affected systems and devices back into normal operations and further strengthen the systems in order to mitigate or prevent similar instances by
- Restoring of systems from clean backups
- Rebuilding systems from scratch
- Changing credentials
- Assessing and Tightening network security
- Installing patches and other tested updates
- Replacing compromised files with clean versions
Post Recovery -Lessons learnt from the incident must be documented and the Incident response plan/ disaster recovery plan is to be updated to reflect the changes made to further foolproof the plan.
Recovery procedures are to follow the identification, collection, acquisition and preservation of information pertaining to the event which can serve as evidence while performing forensics investigations.
Based on the significance of impact of the Information Security Incidents, the government organization should report cyber security incidents to Sri Lanka CERT via Report Incident (cert.gov.lk).



 Total Users : 228399
Total Users : 228399