Online Safety

What are the types of threats that an entity can be subjected to in terms of Cyber incidents?
There are many types of cybersecurity incidents happening every day irrespective of the field, business. Defense, Governmental institutes, Finance, Medical, Education were few fields mainly targeted by attackers in recent years. However, cyber threat actors target individual personnel and normal home internet users as well.
The intentional or accidental incidents which may occur due to the malicious behaviours of current and past employees, third party service providers that work with company information and/or information systems. For example, a disgruntle employee may try to leak confidential data to a competitor, a reckless employee may install a malware on the IT network accidentally. Proper user activity monitoring, malware management, physical and logical access controlling, providing user awareness training are few actions a company can take to minimize the impact of insider threats.
This kind of attack can be occurred physically or logically. Stolen credentials can be used to access systems/ data logically whereas unauthorized visits to restricted areas using methods like piggy-backing and perform malicious activity, stealing of important documents are examples for physical security breaches.
Imposing proper logical and physical access controls, access log monitoring, implementing secure storage mechanisms such as encryption for logical data storages and using safes to store important physical documents are few security controls to minimize the risk.
An attacker usually uses a configuration error, programming error or another vulnerability to gain access to an application or a system and upgrades his access level to a high level privilege such as administrative access. The attacker will start to steal / manipulate data, install malware on the network using these elevated privileges.
The IT network can be protected from escalation of Privilege attacks by patching the systems regularly, conducting application security reviews and fixing identified errors, privilege access management and monitoring.
An attacker uses phishing e-mails containing malicious links or attachments. These emails are disguised as legitimate ones hence the users are easily lured by them. Phishing attacks are used to steal login credentials, install backdoors on the IT network. Certain attackers send malicious e-mails targeting a specific person or a group of people, mostly the members of executive management. This type of attacks are knows spear-phishing attack. User awareness, network behavior monitoring, malware management tools are few safeguards to protect the company from phishing attacks.
There are numerous types of malware attacks. Botnets, Ransomware attacks, Trojans, Remote Access Trojans (RAT), Rootkits & bootkits, Spyware, Adware, Viruses & worms are main types of malwares. An existence of a malware can be identified by unusual behavior patterns on the systems and/or network. For instance, slow speed, high network traffic utilization, crashing or freezing of systems, sudden loss of disk capacities, pop-up advertisements are such anomalous activities. Most of the malware is unknowingly installed on the company’s IT network when an employee clicked on a malicious link or downloaded and opened malicious attachments/ software. These links, websites, attachments are usually disguised as legitimate ones.
User awareness training, Malware guards, user activity controlling and monitoring are few precautions that can be taken to minimize the threats due to malware.
An attacker sends a large number of requests to the targeted system than the number of request it can handle causing it to crash. The intention of a DoS attack is to disrupt the service of a system or an entire network. DoS attacks can be prevented by configuring firewalls and routers to block the fraudulent traffic.
In a MitM attack, an adversary secretly intercepts a communication occurring between two parties and steals and/or manipulates messages. Session high jacking, Wi Fi Eavesdropping are the examples of MitM attacks. Implementing encryption protocols such as TLS, SSH will secure the network communications from MitM attackers.
There are various types of web application related attacks. OWASP.org provides a comprehensive and updated list of web application vulnerabilities every year. According to OWASP, the recent mostly exploited Web application attacks are;
- Injection attacks (Injection flaws, such as SQL, NoSQL, OS, and LDAP injection)
- Broken authentication
- Sensitive data exposure
- XML external entities (XXE)
- Broken access control
- Security misconfigurations
- Cross-site scripting (XSS)
- Insecure deserialization
- Using components with known vulnerabilities
- Insufficient logging and monitoring
Software developers should follow secure development life-cycles (SDLC) when developing applications. Conducting code reviews will help to identify the weaknesses in applications and implementing a Web Access Firewall (WAF) will prevent many web application threats.
An attacker tricks victims via verbal communications (telephone calls or face-to-face discussions), using e-mails and social media platforms to gain system access, physical access or certain information regarding the organization or its employees. To minimize the risk, proper user awareness training should be provided to educate people about social engineering attacks.
In an APT, the attacker gains access to a network and remain undetected for an extended period of time. The usual goal of an APT is to monitor network activities and steal data rather than disrupt the IT network or organization. Networking traffic monitoring can help organizations prevent intruders from installing backdoors and extracting confidential data.
Basic Methods of safeguarding a business from cyber attacks
Taking a business online has a vast amount of benefits but at the same time, it may bring various cyber threats as well. Therefore, the companies should implement a cyber security programme to minimize these threats in order to protect the business, the employees and its customers.
If you are an owner of a business or someone designated to build data security procedures from the scratch for the first time, the prime thing which comes to your mind is from where and how to start security.
We will discuss the basic but important technique of developing a data security programme for your company, in this article.
It is always recommended and better to have a qualified and knowledgeable person or a team to take care of information security, so that this person and/or team will keep the security journey of the company going on continuously. This would be more effective if an organization can appoint a competent person to the C-Suite as the Chief Information Security Officer.
However, it is understandable that this is not possible for certain small or medium sized businesses (SMBs) as they operate with a limited human resources and financials. If your business runs on a digital platform, it will be still worthy to appoint a team within the company with suitable members who can make proper decisions and implement those safeguards.
After all, security is a responsibility of everyone.
Understanding the nature of the business, type of data processed within the business and the stakeholders of the company will be useful to identify a suitable approach and a security framework for the company.
It is necessary to know your information assets. They can be the computing devices, network devices, special software/ applications which runs as the core of the business, data (Financial, Customer, Secret recipes, future plans etc.). Document all the important assets together with other details about them such as purpose, users, location, asset owners (i.e. responsible personnel to manage the asset), backup details etc. and make sure that the inventory is continuously maintained up to date. A proper asset inventory indicates all the data, data points, the responsible parties etc. Hence, it will be really helpful when managing the security of company’s data.
All company related data should be classified considering the sensitivity and consequences which will occur if they get exposed. This will give a correct direction to enforce laws and implement rules within the organization to safeguard the information.
It is essential to conduct a Gap Analysis to identify all the information security related loopholes of the company. All technical and procedural weaknesses should be identified at this point. If the organization does not have anyone who is capable of performing such an activity, you can outsource the experts. An organization can follow a security standard ISO 27001:2013 to carry out this process.
The gap analysis gives a clear picture about the current security posture of the company. Therefore, making it easy to take decisions on essential improvements, prioritization of requirements based on the risk exposure and impact to the business.
Below mentioned areas should be assessed during the gap assessment.
- Human resource security – to identify the threats which may cause by the people involved in the business.
- Asset management – to identify information assets and whether appropriate protection responsibilities are implemented.
- Access control – ensure that employees can only view information that’s relevant to their job.
- Physical and environmental security – to assess unauthorised physical access, possible causes of damage or interference to data processing premises due to man-made or environmental disasters.
- Operations security – ensures that information processing facilities such as malware management, data backing up, event logging and monitoring, technical vulnerability management, periodic security audits are in place.
- Communications security - Network security management, ensuring that the confidentiality, integrity and availability of information which is processing, in transit and at rest.
- System acquisition, development and maintenance – security concerns when purchasing third-party software and/or when developing systems internally.
- Supplier relationships – protection of information assets that are accessible to, or affected by, third party service providers and maintain the agreed level of information security and service delivery.
- Information security incident management – ensure that an information security incidents are identified, reported and appropriate decisions are made by a designated team to remediate the on-going incidents and to prevent future.
- Business continuity management – Information security aspects of continuing the business processes without or with minimum disruptions during a disaster.
- Compliance – identify their legal and contractual requirements, mitigating the risk of non-compliance and the penalties that come with that.
All staff members must be educated regarding the importance of securing company information, their responsibilities towards it and about the possible pitfalls such as phishing e-mails, social engineering etc. which they may fall into and harm the organization. By creating a proper corporate security culture, the employees will be more concerned, responsible and supportive on protecting company data rather than expecting that only the Information Security team is responsible to protect the company from IT related threats.
It is essential to document all the information security policies and procedures which have been imposed and implemented in the company and update them whenever a change is done. All employees should understand the company’s security policies and abide by them.
How can a datacenter of a company be secured?
Before entrusting your data to a center, be sure that the colocation facility is situated in order to be impervious to the elements, including floods, earthquakes, tornadoes, etc. Some companies are even choosing to locate their centers in underground areas. Avoid following areas;
- Airport landing paths
- Power plants
- Flood plains
- Earthquake fault lines
- Proximity to chemical facilities
- Other areas commonly experiencing natural disasters (Tsunamis, wild fires, hurricanes, tornados, etc.)
Data centers may have at least two access points: a front entrance for customers and staff and a back loading dock. If extra fire exit doors are required, build them with no handles on the outside so that they can be used only as ways to leave the building.
Barriers such as fencing, thick concrete walls, lone-standing retaining walls and underground environments are some of the physical security that data centers can offer.
Monitor everyone who comes and goes. Should maintain a complete list of everyone who is allowed access, and privileges should be revoked immediately when no longer necessary.
- Multi-factor authentication
- Multiple checkpoints throughout your facility
- Locks on all server cabinets and Biometric
- Mantraps with an airlock between two separate doors, each of which requires its own authentication
- Surveillance Monitoring Systems
- Redundancy with power supply
Protect against advanced persistent threats. In order for this type of system to be effective, it requires real-time monitoring to catch abnormal events when they are occurring. These include increased service requests, the sudden appearance of large data sets that move erratically around the environment, exportation of unusually large amounts of information from the network, increased phishing attempts and odd user accessing behaviors.
One of the most popular of the newer technologies, and many providers find that it is a very helpful aid in providing data center security best practices. These complex systems manage all facets involved in the running of a building, including fire alarms, ventilation, access and climate control.
Enable network-level encryption to monitor and perform analysis of all traffic occurring during data transfers. Be sure that traffic is segmented at the software level based on endpoint identity.
Employ traditional threat monitoring and protection strategies for asset protection and minimization of vulnerabilities such as:
- Net flow analyzers and isolators;
- Spam, content, network, packet and virus filtering;
- Encrypted communications
Use a virtual firewall to protect customers from outside network activity such as packet injections. The virtual firewall is a supplement to the physical firewall that the data center provider will already have.
The standards help to define or provide a guide on the minimum requirements and best practices to observe, when setting up and operating a data center.
- Telecommunications Infrastructure Standard for Data Centers (TIA-942)
- ISO / IEC 27001:2005 and 27001:2013 Information Security Management System Standard
- NIST 800-171
Is it possible to verify the authenticity of an email I receive?
Without a doubt, electronic mail (e-mail) has become a fundamental requirement in enterprise functionality. With the increase of mobile device usage, emails are now at the tip of your fingers, making it the most convenient and accepted method of official communication. Inevitably increased usage of emails globally has allowed cyber attackers to exploit the susceptible nature of human beings. “Phishing” is an attack vector in which a targeted individual or an organization is contacted via email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. Email phishing has always been a popular weapon of a cyber attacker’s arsenal. A successful phishing attack can result in device or network compromise, stealing of credentials, data theft or even ransom attempts. Therefore, verifying the authenticity of an email received by an individual becomes the first and most crucial defence strategy.
Although modern day spam filters are continuously monitoring for suspicious emails, they cannot be considered as an airtight solution for rapidly evolving sophisticated phishing emails originating from various parts of the world. As the first line of defence, it is imperative that the user posses enough knowledge and knowhow to detect a possible email which could lead to a phishing attack.
The easiest yet an effective starting point for a user is to verify the sender of an unauthenticated email. Once an email is received from an unknown entity, the user may hover the mouse pointer over the ‘From’ display name to verify the email address associated with the sender name. Although an attacker might use a convincing Name to assert legitimacy, further inspection of the email address can reveal the real identity of the sender. There can be attempts when the attacker uses extremely legitimate looking email address as the Name of the sender. This can be confusing as the real email address can only be seen upon expanding the sender section by hovering. Figure 1 below depicts a scenario of an email which bypassed the Spam filter and where the attacker uses a legitimate looking sender name(Email Address), however further inspection of the sender email address clearly indicates that is a phishing attempt. In this case the authentic sender email domain should be sendername@bt.com.
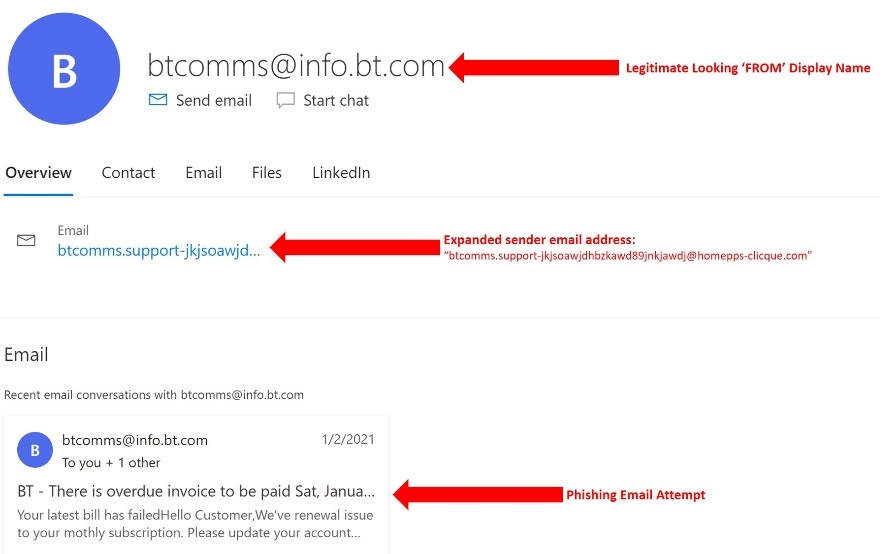
Figure 1: Identifying a phishing email using sender address and domain name
It is also important to note that there can be attempts when an attacker uses a domain name that can look almost identical to the legitimate domain barring minor character changes.
As a secondary investigation user may inspect the email content itself. Here the user should be extremely careful not to click on any of the links. The objective here is to inspect for the following clues.
- Urgency: Trying to rush the reader to carry out an action such as fill out a form before a deadline or an expiration
- Poor composition: Indications of trying hard to be 'official', usage of unusual phrases or colloquialism, spelling mistakes and incorrect grammar
- Asking for personal or bank details
- A link to be clicked: A link which redirects to a different domain compared to sender name
Links in the body of an email is the biggest clue to spot a phishing email. Without clicking on the link, user may hover over it to see where the destination is. Standard web browsers indicate the destination at the bottom left corner when hovering over a link (Figure 2).
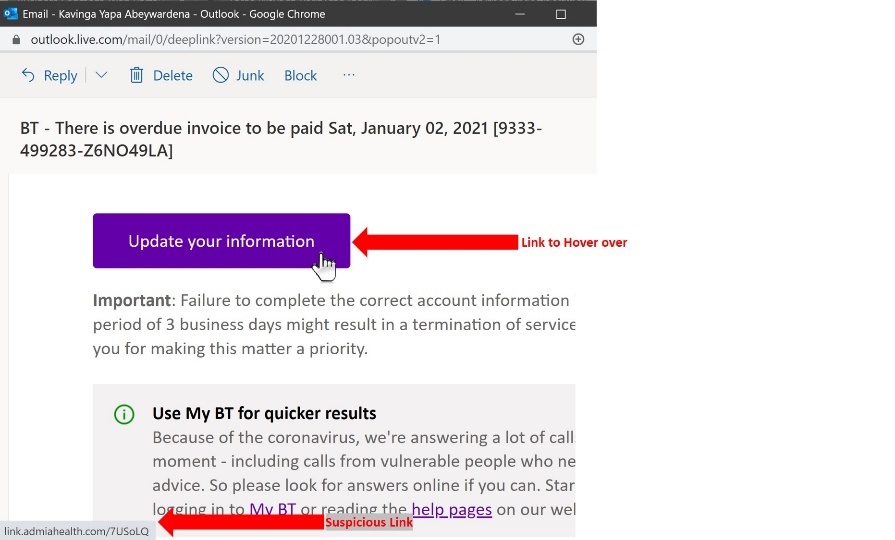
Figure 2: Identifying a phishing email using link hovering
If you are still unsure about the authenticity of the email, it is recommended to get an expert opinion prior to download an attachment or clicking on any of the links.



 Total Users : 228417
Total Users : 228417